https://www.ikarussecurity.com/wp-content/uploads/2024/04/benutzerkonten.jpg
400
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2023/09/IKARUS-Security-Software-1.png
IKARUS2024-04-10 14:11:292024-04-10 14:11:30Account management: The underestimated risk of forgotten user accounts
https://www.ikarussecurity.com/wp-content/uploads/2024/04/benutzerkonten.jpg
400
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2023/09/IKARUS-Security-Software-1.png
IKARUS2024-04-10 14:11:292024-04-10 14:11:30Account management: The underestimated risk of forgotten user accounts5.9 million US dollars, the company’s business ability and that of its business partners are at stake after the ransomware attack for the American agricultural association NEW Cooperative Inc. Company. Data was stolen, computer systems encrypted, and the company had to take its systems off the net in a first step. The impact of the attack on regional food and livestock supply is still unclear.
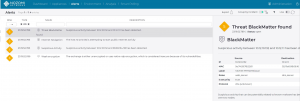
Nozomi users who use the Threat Intelligence Service are actively protected from the BlackMatter ransomware.
IKARUS partner Nozomi Networks has subjected the ransomware to a detailed analysis. All findings are continuously fed into the Nozomi Networks Threat Intelligence: Companies that use the service in conjunction with Guardian appliances for network monitoring are already actively protected against the BlackMatter attacks.
BlackMatter: Anti-debugging techniques, configuration and IoCs
According to the analysis, BlackMatter uses a version of the ChaCHa20 and RSA algorithm to ensure that the victim’s data cannot be decrypted without the attacker’s private key. In addition, local backups and recycle bin contents are deleted, processes and services are terminated according to configurations. Also, the desktop background is changed, user account control is bypassed, and encrypted files are enhanced with a victim ID according to MachineGuid Registry.
In addition, BlackMatter can prevent malware analysis by concealing which WinAPIs it relies on and responding specifically to debugging signals. OT security specialist Nozomi Networks publishes in a blog post the most important decrypted strings from his analysis as well as some scripts that can help other researchers extract key information from other instances of this ransomware that appear in the wild. In addition, the article contains a list of the identified Indicators of Compromise.
Prevention & Detection: Real-time monitoring of IT, OT and IoT systems
Ransomware no longer only threatens the IT systems of companies but also industrial security. Nevertheless, certain convergence is possible. “My most important tips besides technical measures for real-time detection of threats and anomalies: Protect your backups from ransomware!” says Industrial Cyber Security expert Herbert Dirnberger from IKARUS.
For more information on how to protect your IT, OT and IoT environments against ransomware and other cyber threats, visit https://www.ikarussecurity.com/en/it-ot-and-iot-security/.
Contact us on +43 1 58 995 500 or sales@ikarus.at!
Worth reading:
Who takes care of security in the OT?
Sources:
Behavioural analytics, anomaly detection and visibility: additional protection against ransomware